If you’re like me, you rarely ssh into your vCenter appliance as “root”. However, the time comes when you need to update vCenter, you run the “Pre-Update Checks” — and because you never log into the appliance — you get the message that your root password needs to be updated before you can install the update.
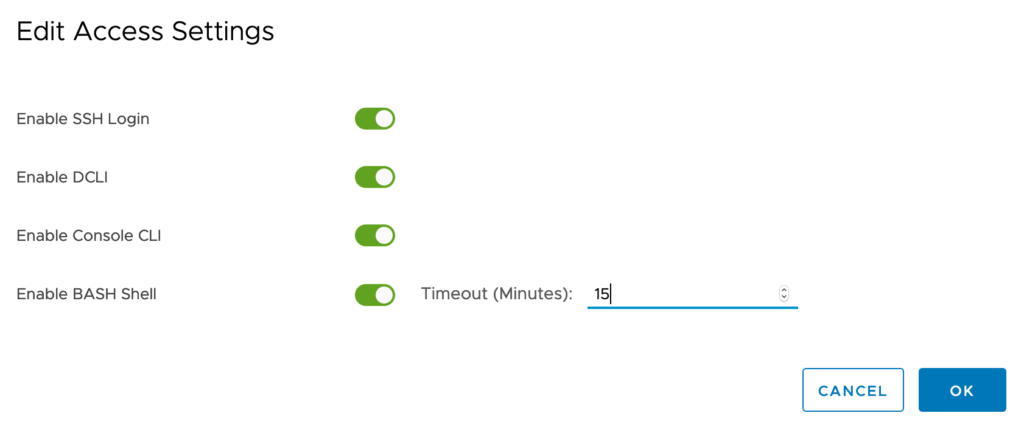
So… log into the vCenter Service Management Console (https://your-vcenter:5480), click Access and then Edit. Make sure that SSH Login, DCLI, Console CLI, and BASH access are all enabled. Set the BASH timeout to 15 minutes so it gets disabled automatically when you’re done.
Once you’ve done that, ssh to the appliance.
$ ssh root@vcenter.labs.earlruby.org
VMware vCenter Server 7.0.0.10700
Type: vCenter Server with an embedded Platform Services Controller
Received disconnect from 192.168.200.11 port 22:2: Too many authentication failures
Disconnected from 192.168.200.11 port 22Did you get a “Received disconnect … Too many authentication failures” message? Don’t worry, no one is hacking into your vCenter, it’s just that you have more than one ssh key on your keyring and for some reason someone at VMware thought that it would be a great idea to set the vCenter ssh setting MaxAuthTries = 2. Your first ssh key counts as one try, your second ssh key counts as attempt number 2, and… you’re done. vCenter won’t let you log in.
To bypass public key authentication checks entirely use the -o PubkeyAuthentication=no parameter for ssh:
$ ssh -o PubkeyAuthentication=no root@vcenter.labs.earlruby.org
VMware vCenter Server 7.0.0.10700
Type: vCenter Server with an embedded Platform Services Controller
root@vcenter.labs.earlruby.org's password:
Connected to service
* List APIs: "help api list"
* List Plugins: "help pi list"
* Launch BASH: "shell"
Command>Now get to the bash shell by typing shell, then passwd to set the new password, and you can update the root password:
Command> shell
Shell access is granted to root
root@vcenter [ ~ ]# passwd
New password:
Retype new password:
passwd: password updated successfully
root@vcenter [ ~ ]# exit
Command> exit
Connection to vcenter.labs.earlruby.org closed.Before you log out, run the Pre-Update Check again to verify that vCenter sees that the password has been updated. This time you should get the message “No issues found. Pre-update checks have passed.”
Hope you find this useful.