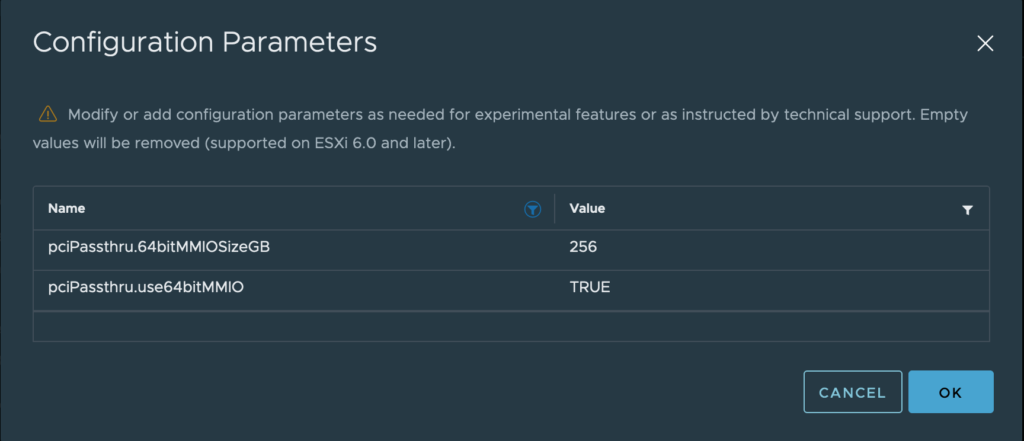
Got an interesting error on Gitlab today. On an MR that had passed tests and had been approved, Gitlab would not allow the branch to be merged because “The source branch [Branch Name] does not exist. Please restore it or use a different source branch.”
Checking the “Changes” tab in Gitlab showed all of the changes that I expected to see. So Gitlab could see the changes and knew the branch name.
I checked the commit SHA connected to the branch, and Gitlab showed all of the changes that I expected to see. Gitlab knew the correct SHA and was associating the SHA with the branch name, but the “Overview” tab still showed the error message “The source branch [Branch Name] does not exist. Please restore it or use a different source branch.”
I Googled to see if anyone else had had the issue. Many people had. This issue report on Gitlab.com shows that the problem goes back at least 3 years. The official response from Gitlab is that “This is no longer an active issue.”
I beg to differ. I’m using GitLab Enterprise Edition 14.8.6-ee and it still has this issue.
I cloned a fresh copy of the repo from Gitlab on my laptop and checked the branches with:
git branch -a
The branch was listed. I checked it out. It checked out just fine. I diffed it against the main branch. All of the changes were present.
So the branch exists on the repository on the server, it has all of the changes in it that I expect, there is nothing wrong with the Git repo itself, it’s just Gitlab that has some sort of disconnect.
To work around the problem I added an empty commit to the branch and pushed it to the Gitlab repo:
$ git commit --allow-empty -m "Empty commit"
$ git pushOnce I did that the error message cleared. Gitlab had to re-run the tests, but once the tests passed I could merge the branch.
Hope you find this useful.
Update: I spoke to one of the people who manages GitLab Enterprise for my team and apparently Gitlab works by scraping the Git repo for updates and changes using a “scraper service”. If the service is off-line or reset at the time your commit is pushed it’s supposed to pick up any missed pushes when the service restarts, except sometimes it doesn’t work.
As long as the service is on-line the next time you push a commit then Gitlab will pick up the new commit and any missed commits, and everything will be back in sync.